A team of researchers from Standford has presented a project to create reversible transactions on Ethereum (ETH). If this concept is ever realized, it would create a new family of tokens: the ERC-20R and ERC-721R.
The concept of reversible transactions on Ethereum (ETH)
Kaili Wang, a researcher at Stanford University, has presented a white paper in which she and several of her colleagues describe a concept of reversible transactions:
Billions in crypto stolen. If we can’t stop thefts, can we reduce the harmful effects?
Over recent months, a couple other @Stanford researchers and I drew out and prototyped ERC-20R/721R to support reversible transactions on Ethereum
See post :https://t.co/38Hs0F9goU
– kaili.eth (@kaili_jenner) September 24, 2022
The researcher explains that the idea for the project came from the range of hacks that the ecosystem has faced. She cites attacks such as the $320 million Wormhole bridge, or the various phishings of which some Bored Apes owners were victims, for example.
It is true that in these cases, a “back” button would be useful. However, the idea may seem counter-intuitive, as the very essence of a blockchain is to be irreversible.
Of course, the aim is not to make the entire Ethereum blockchain reversible, as that would make no sense. Instead, it would be through a new standard of tokens, which could be used for strategic cases: the ERC-20R and ERC-721R.
The concept would be that after an error in a transaction, or a hack, we could make a claim in a decentralised court, to claim the return of the assets.
The concept of the decentralised court
The ERC-20R and ERC-721R would be built by implementing various functions in such a way as to enable challenges. The diagram below shows how these functions are called upon during the process:
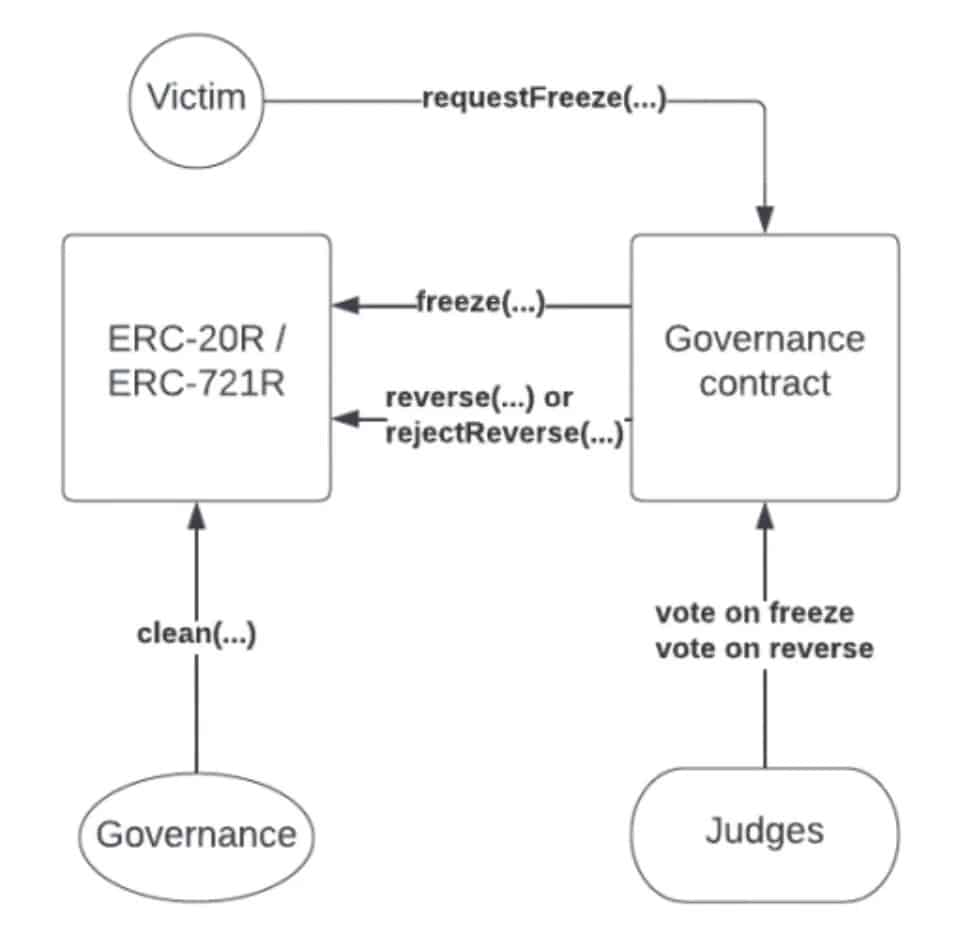
How a reversible transaction works
The victim actually calls a function called “requestfreeze(…)” which triggers the “trial”. First, the governance judges of the project to which these tokens belong vote on whether or not to freeze the assets, which will call the “freeze(…)” function. Then, after another vote, these same judges will decide whether to use the “reverse(…)” or “rejectReverse(…)” function to return the tokens to their original owner.
The white paper for this hypothetical category of tokens explains in detail how this algorithm works, however, several limitations can be observed.
For a non-fungible token (NFT), it is very easy to know exactly which address it is located at, but what about fungible tokens? Let’s take the example of 10 stolen A tokens, which would be sent to another address already containing 10 other “clean” A tokens. Then the owner of this address sends them to two separate addresses in equal amounts.
In this example, it is not possible to know exactly where the stolen tokens are, yet the algorithm would only target one address.
While the reversible transactions presented by Kaili Wang are interesting, we note that in the case of a hack, one would have to react very quickly, as the “window of opportunity” would be very limited.
Such a technology could not be applied to the whole ecosystem, but if it were to emerge, some decentralised autonomous organisations (DAOs) might for example find it interesting to adopt it for their governance tokens.
