On Reddit, a fraudulent article posing as our Blockworks colleagues has been relayed, pretending to be a Uniswap hack to share a phishing link. How does this scam work and what can we learn from it?
Fake Blockworks site tries to trick readers with phishing link
On Reddit, several subreddits were shared giving the illusion of an article by our Blockworks colleagues informing of an alleged $37 million hack on the decentralized exchange (DEX) Uniswap (UNI):
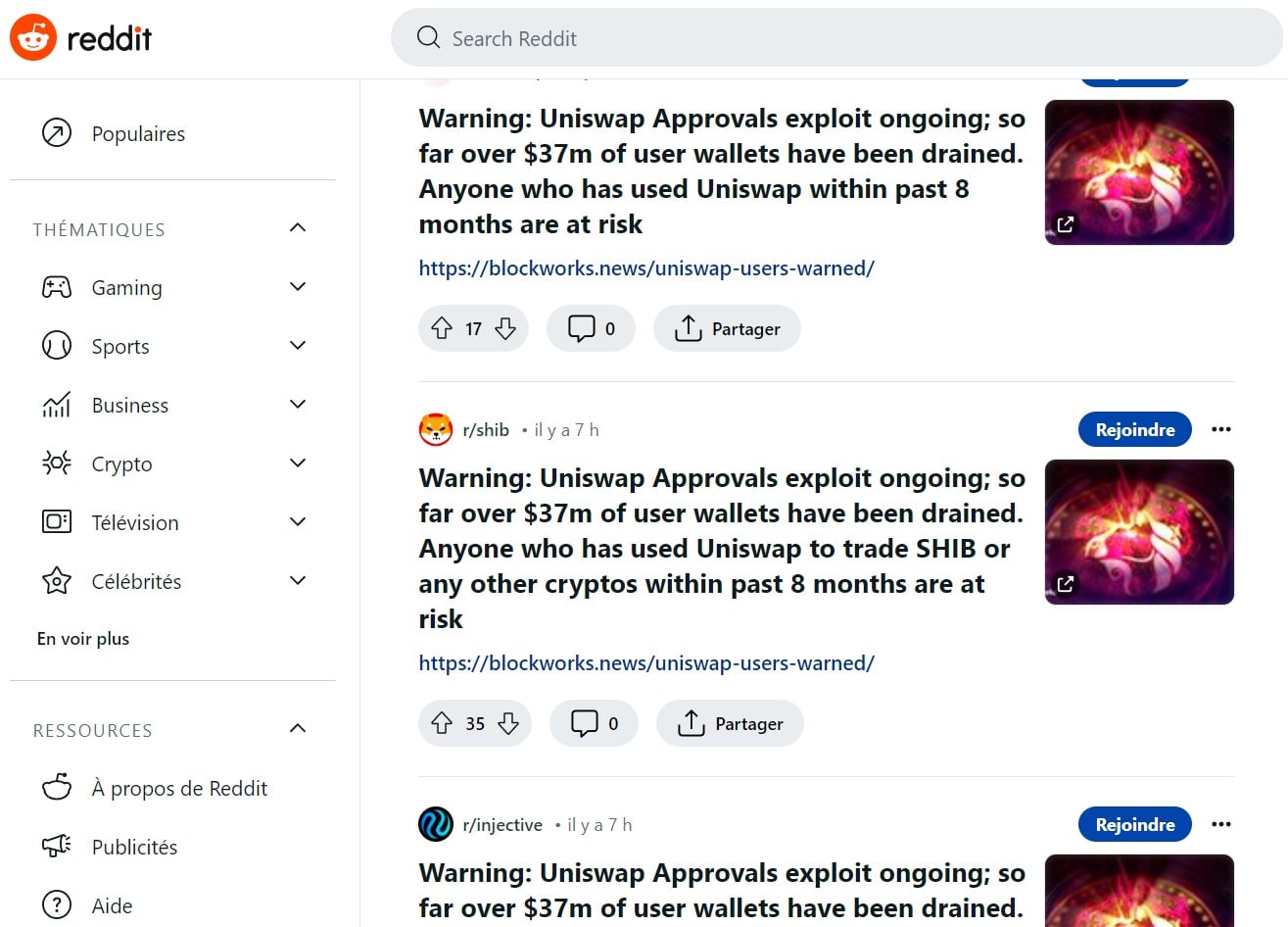
Figure 1 – Fraudulent subreddits warning of an alleged Uniswap hack
Once on the article, we notice that the website looks almost exactly like Blockworks’. The said article consists of a few vague details about this fake attack, incorporating fake quotes from real people in the ecosystem and, above all, inviting readers to go and revoke approval on a supposedly compromised smart contract.
A crucial point is actually to be found in the domain name used here, which is “blockworks.news” while the real URL of the media is “blockworks.co” :
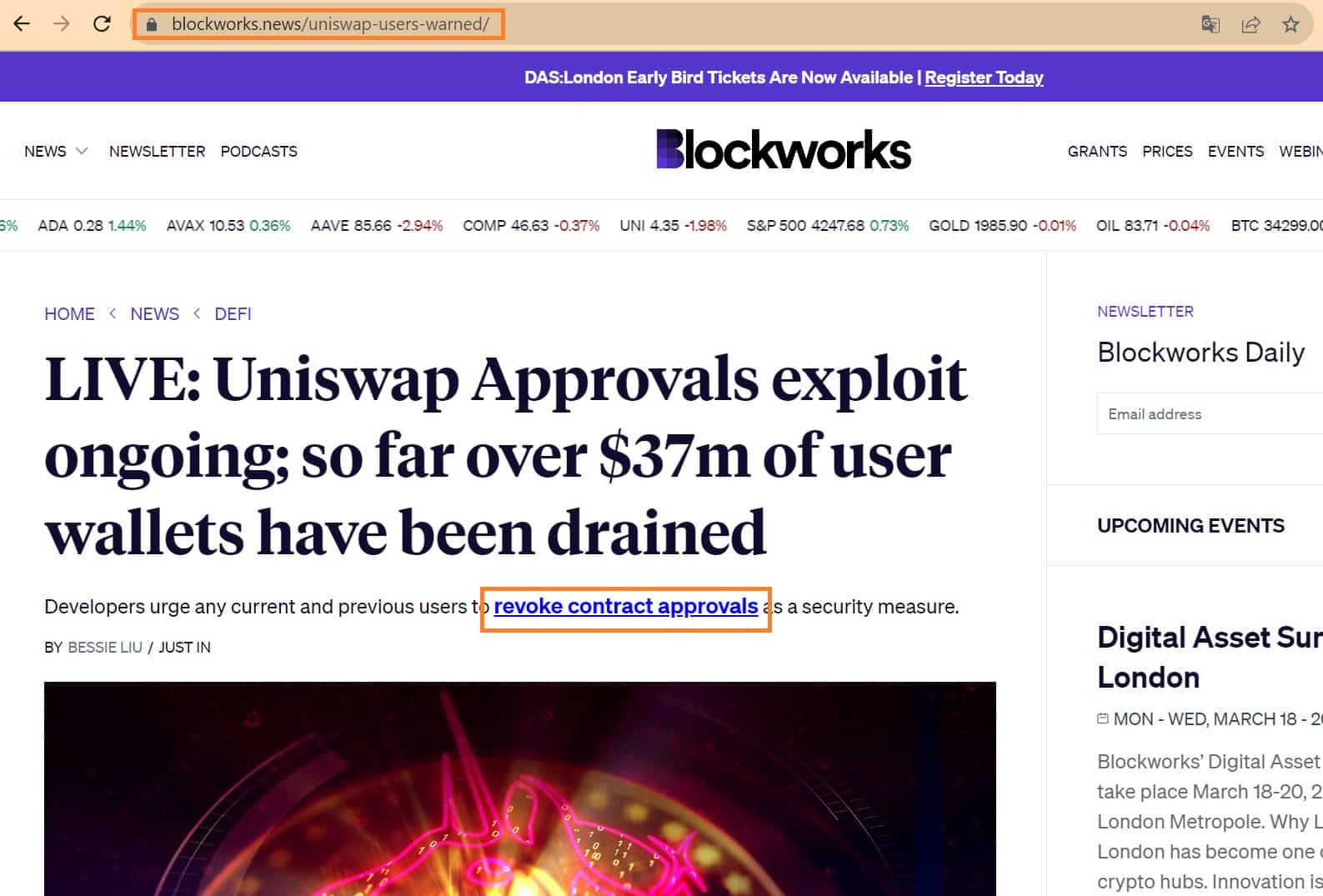
Figure 2 – Fraudulent phishing article on the fake Blockworks website
To push the vice even further, all clickable links on the fraudulent site outside the article link to real Blockworks addresses, leading the user to believe that they haven’t changed websites. Entering “blockworks.news” in the search bar also takes us to a fake homepage relaying a direct link to this hack that never took place.
A phishing attempt
In reality, the aim of this fraudulent article is to redirect users to a fake Etherscan website to get them to connect their wallet. Again, the website is in every way similar to the real Etherscan, with menus and other clickable links pointing to the appropriate places on the legitimate site.
However, this time we see that the URL doesn’t match at all, the real Etherscan address for revoking smart contract approvals being “etherscan.io/tokenapprovalchecker” :
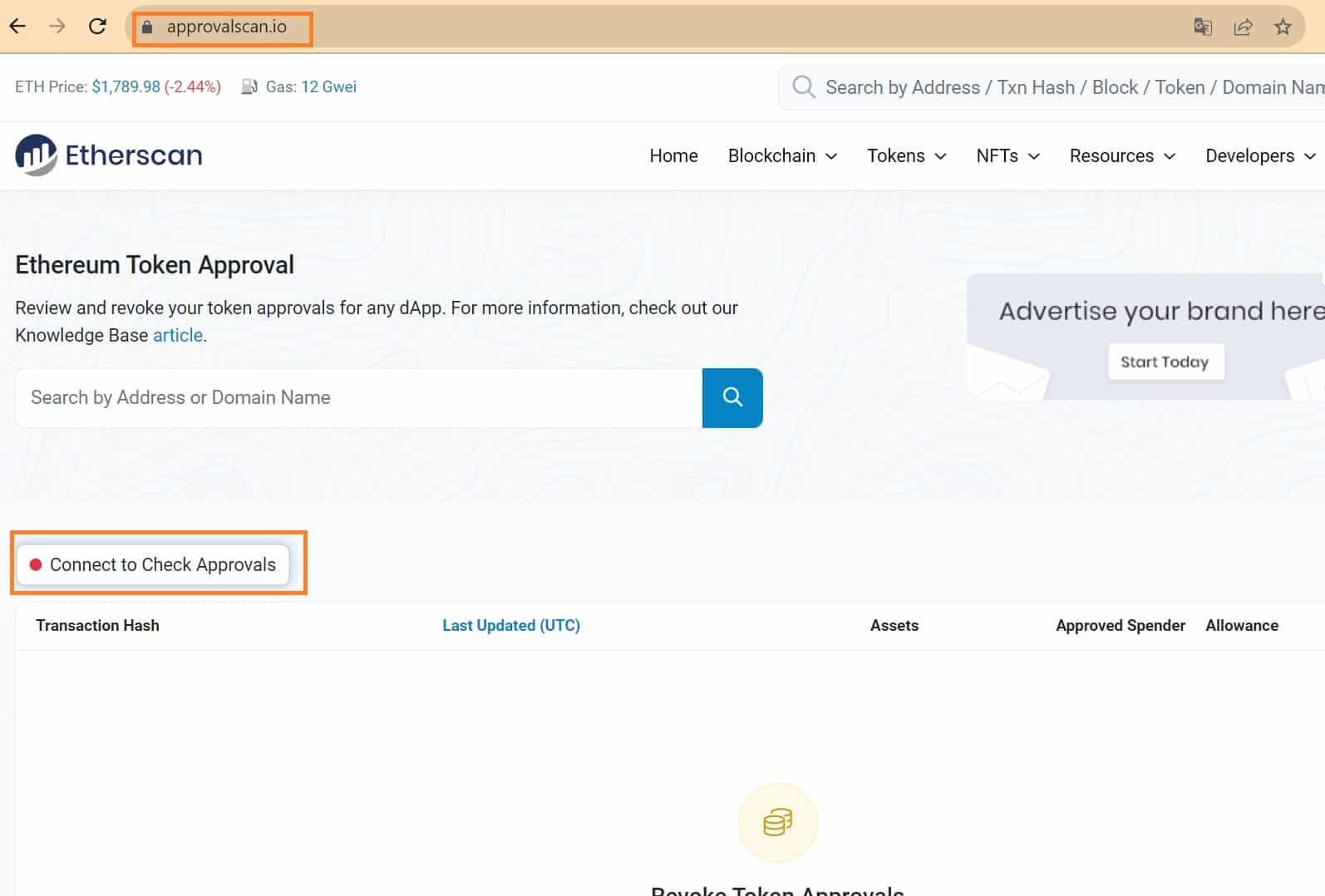
Figure 3 – Fake Etherscan site leading to the connection of a Web3 wallet
Here, it’s a safe bet that by connecting their Web3 wallet to the framed button above, a future victim will authorize a fraudulent smart contract to empty their wallet.
In fact, after trying the experiment with a completely empty test wallet, we noticed that nothing happened. On the other hand, blockchain security company Beosin told our Cointelegraph colleagues that the button isn’t configured properly, as “no phishing transactions are requested after a wallet is connected”.
Nevertheless, it seems that a smart contract has been deployed to empty wallets with a balance of at least 0.1 ETH.
In this case, the scam uses fear to encourage readers to take swift action to avoid a supposed theft of crypto-currencies. In such cases, it’s important to also check the social networks of the players involved and the URLs of the sites you’re visiting, so as to avoid falling into a trap that plays on emotions.
