Recently, a new malware targeting cryptocurrencies has appeared. Its name is Mars Stealer, a Trojan horse that, if it infects your computer, can steal your private keys and other sensitive data. What does it look like?
Mars Stealer targets not only your wallets but also your 2FA extensions
This information highlights one of the most crucial recommendations of our ecosystem: use a hardware wallet. Indeed, a password, no matter how complicated, is insufficient in the world of cryptocurrencies, as well as double authentication (2FA). This is what the Mars Stealer Trojan reminds us.
The information is reported on the Twitter account of programmer 3xp0rt. He sends us to his blog, where he provides a complete analysis of the malware. We learn that this Trojan horse targets more than thirty browsers, including Chrome, Firefox, Microsoft Edge, Opera and Brave.
Mars Stealer attacks crypto wallets that work as browser extensions: MetaMask, Binance Chain Wallet, Coinbase Wallet or Keplr, to name a few. 2FA extensions like Authy or cryptocurrency wallet software like Exodus are also vulnerable.
However, regarding 2FA extensions, only Chromium-based browsers except Opera would be vulnerable.
The main objective of the software will be to steal your private keys. Thanks to this, a hacker will then be able to empty your funds before you know it.
Interestingly, if the victim’s computer is configured in the following languages, Mars Stealer will not perform any dishonest actions:
- Kazakhstan;
- Uzbekistan;
- Azerbaijan;
- Kazakhstan;
- Russia;
- Belarus.
But don’t think that this makes you immune to further attacks of this kind by allowing you to ignore good security practices.
The truth is that Mars Stealer is not the first and will not be the last malware of its kind. Anyone can inadvertently download a program that can steal their private keys or other sensitive data. This is why the most reliable solution to date is the use of a hardware wallet.
With a Ledger key linked to your MetaMask for example, a third party cannot empty your cryptocurrencies, as they would also have to validate the transaction on your key.
Another basic recommendation to limit this type of attack will be to warn you about the software you use. Indeed, a Trojan horse of this kind will often be embedded in supposedly reliable download links. For example, you could launch it thinking you are downloading an ad blocker. For this, choose the site of the software publisher in question whenever possible.
In the same vein, a malicious program could be added to a phishing email, posing as a site you are used to using to get you to perform a particular action.
In this regard, some sites, including Binance, offer to include a phrase or word of your choice in your security settings. This way, when you receive a real email from the site, you will be reminded of what you have entered in a box, as shown in the illustration above with the words “anti-phishing”
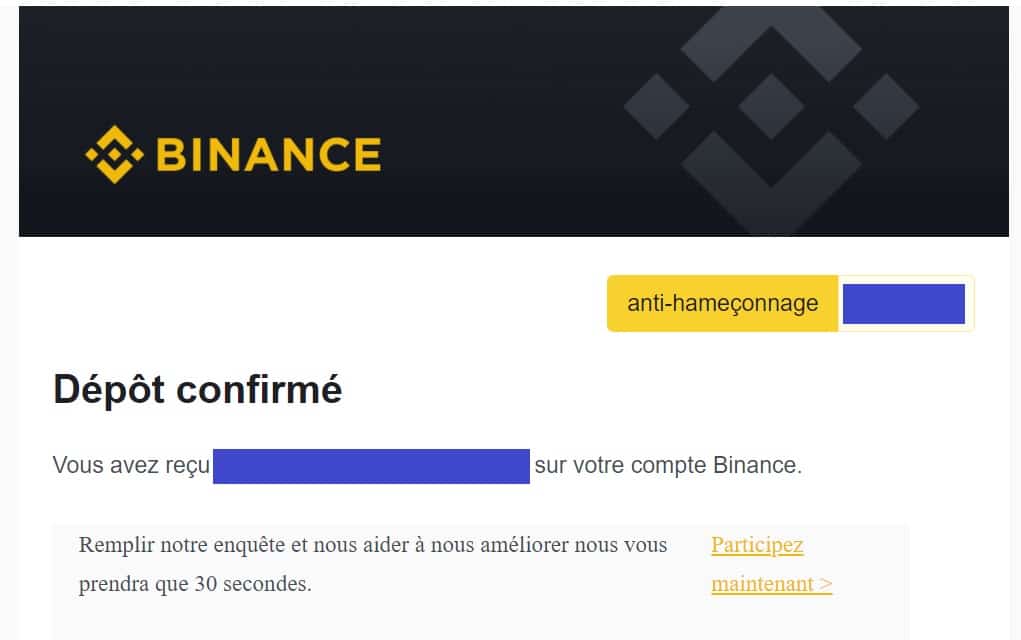
Example of an email from Binance with the anti-phishing code
Despite everything, there is no magic formula to prevent a hacking attempt, but by applying a maximum of good practices, it is possible to limit the risk. Let’s not forget that often the biggest vulnerability is the human being himself
